I’m Ed Skoudis, Founder of Counter Hack Innovations (behind Holiday Hack for 22 years) and President of the SANS Technology Institute. I wrote SEC504 and SEC560, and I love CTFs and puzzles. My steampunk office is packed with antique crypto gear - from an Enigma (A726) to a Gutenberg Bible leaf and a Kryha Liliput.
But right now, I need your help. Our new SOC phishing-triage tool has issues, and sketchy emails are slipping through.
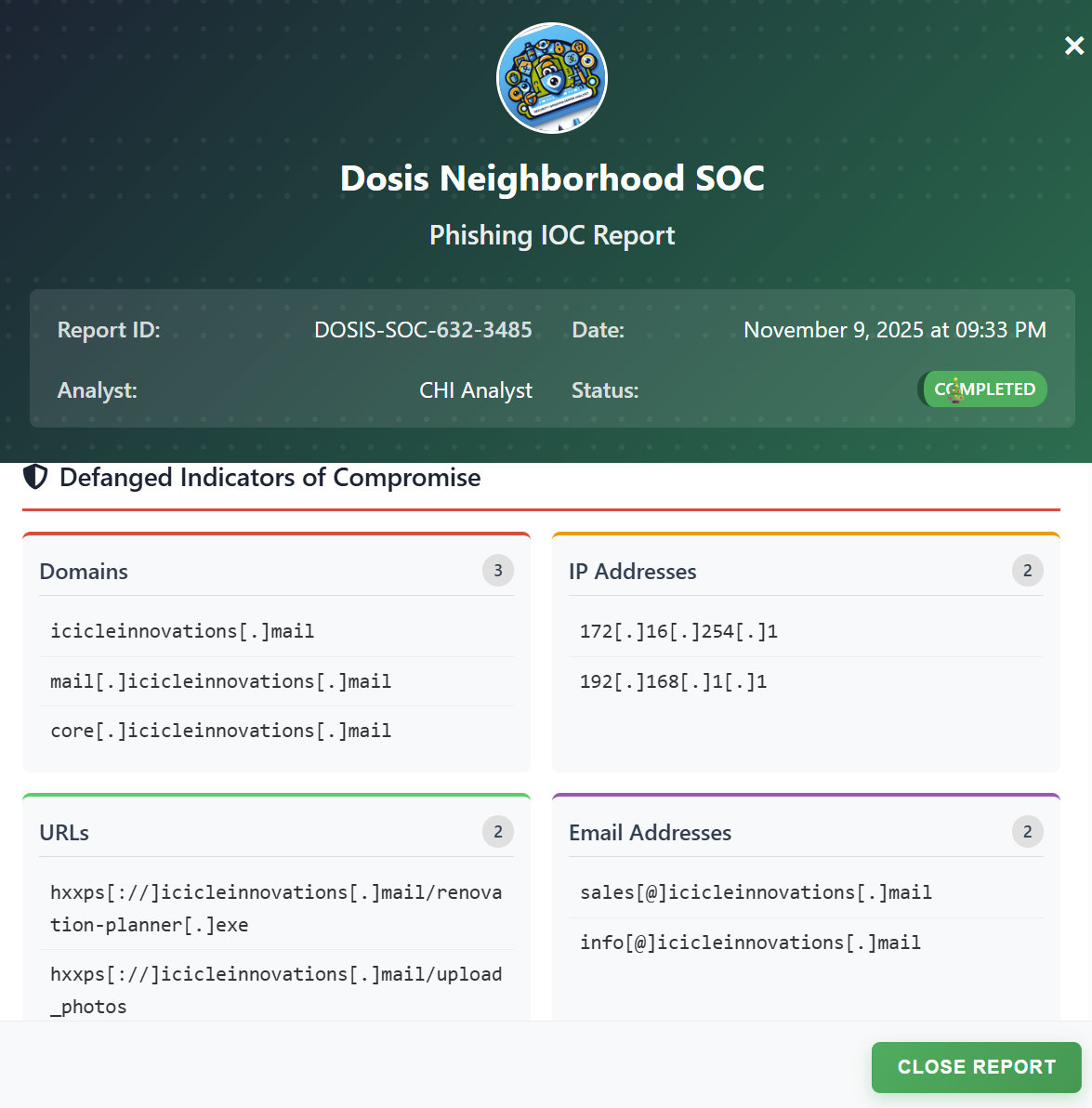
Task: Identify and block all indicators of compromise from the phishing samples so nothing gets past the filters.
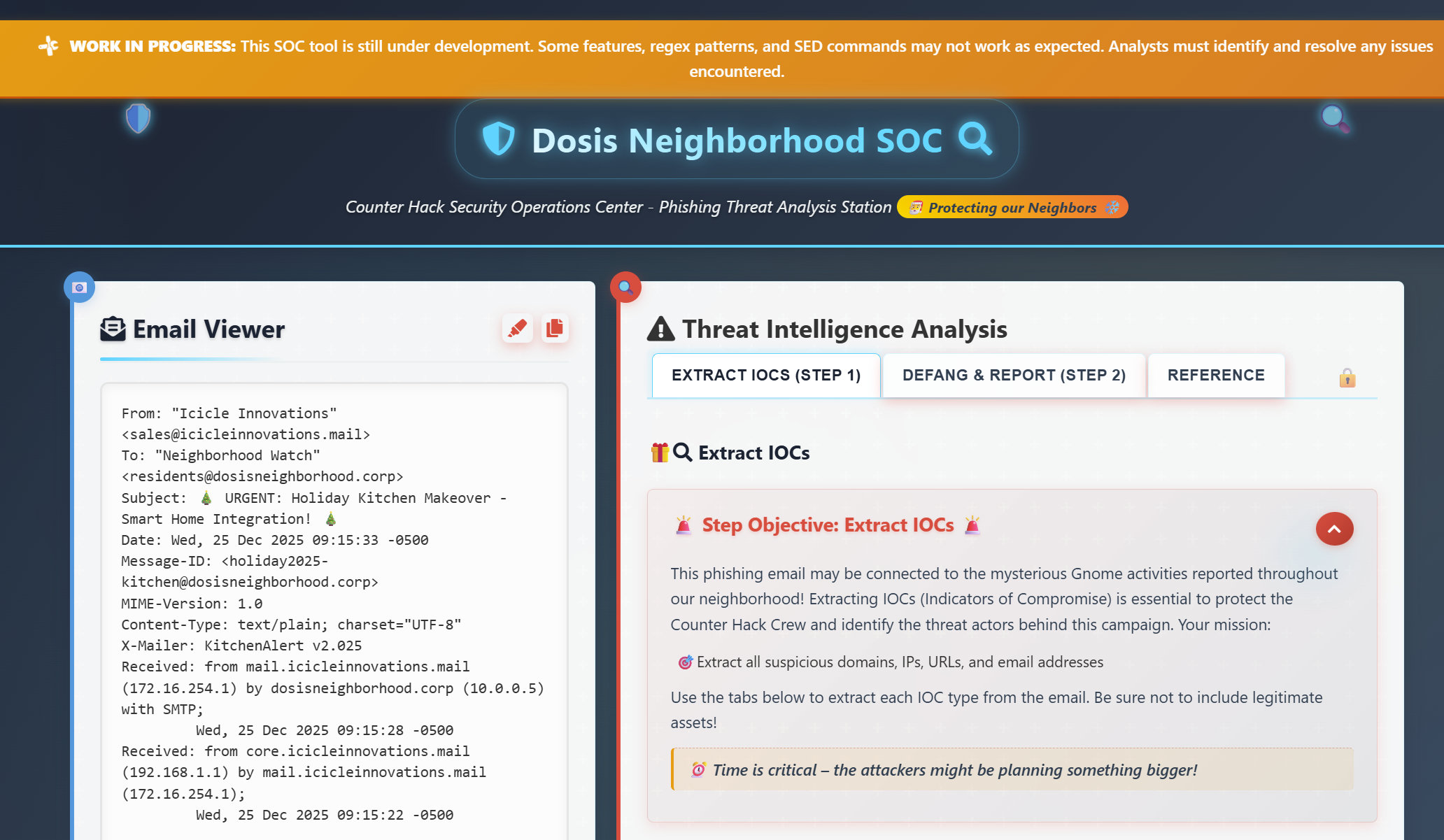
Our mission is to extract all suspicious domains, IPs, URLs, and email addresses.
In the “Reference” tab, we already find helpful regular expressions. However, there are a few errors hidden there that we can easily fix:
Domain Pattern: [a-zA-Z0-9-]+(\.[a-zA-Z0-9-]+)+
IP Address Pattern: \d{1,3}\.\d{1,3}\.\d{1,3}.\d{1,3}
URL Pattern: http(s)://[a-zA-Z0-9-]+(\.[a-zA-Z0-9-]+)+(:[0-9]+)?(/[^\s]*)?
Email Address Pattern: \b[a-zA-Z0-9._%+-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,}\b
However, we then have to remove the IP addresses, domains, and URLs that relate to us from the search results.
Defanging IOCs (Indicators of Compromise) is crucial to ensure that malicious content cannot be accidentally activated. We can use the supplied expressions:
Replace dots/periods with [.]
Replace @ in email addresses with [@]
Replace http with hxxp in URLs
Replace :// with [://] in URLs
All we have to do is connect them together:
Custom SED Command(s):
s/\./[.]/g; s/@/[@]/g; s/http/hxxp/g; s/:\//[://]/g
Now we can submit the defanged IOCs to the Counter Hack Security Team and get the report.